Project Qey-Gen
Qey-Gen, the quantum key generator
Create secure keys by yourself with the quantum key distribution or make a quantum coin toss
Create a secure quantum key yourself and send encrypted messages!
We don’t need photons and elaborate measuring devices! The Qey-Gen is a small wooden box, similar to a piggy bank, into which our quantum coin is thrown. The coin can then be „measured“. Just like the quantum key exchange with photons, depending on the measurement, the correct result comes out, or a random result. In this way, you can carry out the quantum key distribution (QKD) yourself!
If you still want to decide afterwards, you can do a quantum coin toss. The Qey-Gen generates real chance for you!
If you want to make a safe random decision afterwards, you can do a Quantum Coin Toss. The Qey-Gen generates real randomness for you!

You need:
- 1 quantum coin (50 Euro cent coin)
- Wooden components for the Qey-Gen
- 2 list sheets
You can make all the materials yourself. You can find the files in the downloads.
Use 3mm MDF wood panels for the box. We cut them out with a laser cutter.
You can simply paint the coin or cut out stickers with a cutting plotter.
All materials are licensed under a CC-BY-SA licence.
You can also order the set as a tinkering box in our shop.
All materials are licensed by CC-BY-SA-Licence.
Lasercut files for Qey-Gen box (use 3mm Material!)
– Outer box
– Inner box
Plotter files for quantum coin (use 0,50€ Coin)
– Quantum Coin (Plotterfile for Sticker)
– Quantum Coin 1s (2mm Acryl) – Acryl does not work as well as a real coin
– Quantum Coin 0s (2mm Acryl) – Acryl does not work as well as a real coin
Quantum 1×1 makes the most important insights of the quantum world easy to understand. With the help of easy-to-understand videos and the new tinkering boxes, you will gain a basic understanding of second-generation quantum technologies.
You can also orWe visited over 20 quantum experts from different scientific fields. You can discover the conversations on the different topic pages!
Let’s start
⏰ Duration: ca. 90 -120 min
1. Quantum encryption
We constantly send and receive encrypted messages. Usually our smartphone or computer does it automatically.
This encryption is based on mathematical riddles. So if someone had the brilliant idea how to solve these riddles well, it could be cracked. And it is already difficult to exchange the key without anyone listening in.
But with the help of quanta, we could exchange a key absolutely securely and thus also use much more secure encryption methods.
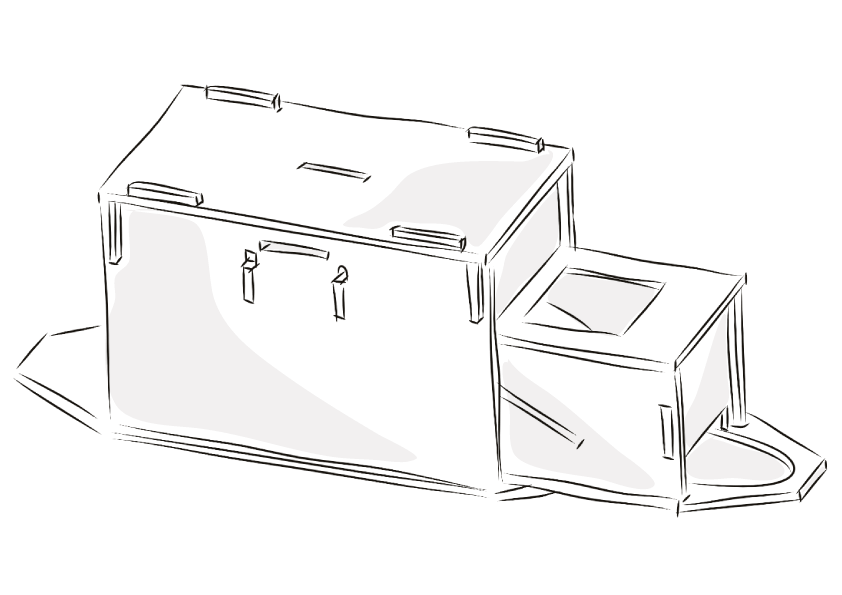
2. Assembling the Qey-Gen
We cut out the components with a laser cutter. The Qey-Gen consists of an outer and an inner box. The inner box is pushed into the outer box at the end like a drawer.
Watch the video or have a look at the instructions (p. 6 to 8).
You can either make the components yourself using the cut files under Downloads or buy them in our shop.
3. How does the Qey-Gen work and how does it relate to quantum physics?
A new way to make encryption more secure is currently being researched. Quantum mechanics is used for this. With this wooden box we can simulate quantum mechanics. But instead of photons and polarisation filters, we use a coin and the Qey-Gen. And you’re still wondering what it all means? Our experts Luisa and Tobi explain what it’s all about.
4. The Quantum Key Distribution (QKD)
With the Qey-Gen, we can perform a quantum key exchange (short QKD). In this way, you can create an encryption key yourself without anyone being able to do a man in the middle attack. In the video you can see how this works with photons. By the way, the procedure is called BB84 protocol. For our experiment we will use a coin.
Measurement
In our example, we call player 1 „Alice“ and player 2 „Bob“ for simplicity’s sake.
Alice secretly slides the coin into slot 1 or 2 and notes the base and value of the coin on her spreadsheet.
Optional:
An eavesdropper could now secretly read the coin in either base 1 or 2 (i.e. open the drawer to the right or left). So that his eavesdropping is not noticed, he slides the coin into a slot again as above. (But in which slot and how does he put the coin? He has to decide that for himself).
Bob makes a measurement in either base 1 or 2 and also notes on his sheet the value of the coin and in which base he measured.

Alice and Bob can then openly discuss in front of the eavesdropper which base they chose for which throw without revealing the value. They cross out all the throws with different bases. They can then use the remaining lines to test whether anyone was listening and, if not, build a key.
Test for eavesdropping
Now the test is carried out to see if anyone has been eavesdropping. To do this, Alice and Bob openly compare
their results for a part of their measurements, e.g. throw 2 and 4.
The encryption key
If there was no eavesdropping, meaning Alice and Bob had the same results for their first measurements, they can build a quantum key from the remaining and still „secret“ or not publicly communicated measurements. In our example, the values for throws 8, 9, 10 and 12 are therefore either „0“ or „1“. Alice and Bob write the quantum key hidden on their spreadsheet. If you have done everything correctly, you should have the same quantum key as a result.
Je öfter ihr den Messvorgang durchführt und je mehr Werte ihr für den Lauschtest vergleicht, umso
The more often you carry out the measurement process and the more values you compare for the test against eavesdropping, the more certain you can be that no one has tried to do a man-in-the-middle attack. You can be sure that no one has tried to read the key during generation. In a comparison, the eavesdropper would have a 50% chance of guessing correctly and not being noticed. With just two comparisons, it is only 25%, with three comparisons 12.5% and with five comparisons even only 3.125%.
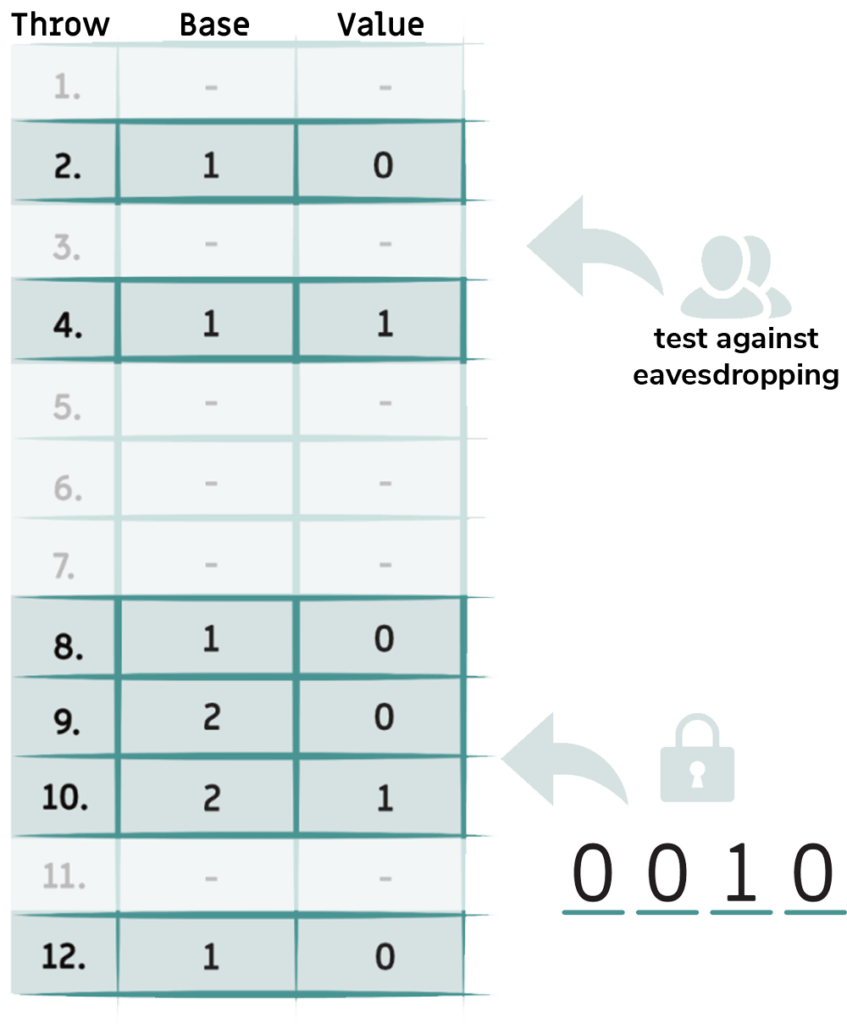
Attention: Since you have already used the first two measured values for the eavesdropping test and thus discussed them publicly, you must not use them for your secret key under any circumstances! The remaining four values, on the other hand, are only known to Alice and Bob and are therefore super safe!
Caesar encryption
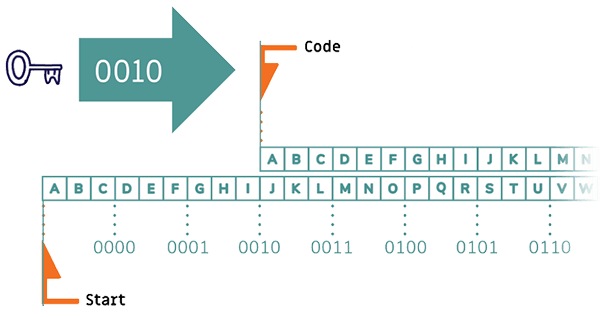
To apply the Caesar encryption with your already created numerical key „0010“, you can use the two strips on your list sheets.
In addition to letters, there are also number marks on it so that you can use your key of zeros and ones to encrypt letters. First place both strips under each other so that the „Code“ and „Start“ markings meet.
Now move the upper strip to the right until the „Code“ marker points to the appropriate key, in this case „0010“.
To encrypt, look for a letter that you want to use in your message in the upper strip. In the message, however, write the letter that appears below it, and your message is encrypted!

Hooray! Now you have created a secure quantum key and you have the possibility to send secret messages to each other.
5. Quantum Coin Toss
Imagine Alice and Bob are talking on the phone. Now they want to make a random decision. For example, who gets to decide what to have for dinner tonight.
Now, for example, Bob could toss a coin and tell Alice the result. But how does Alice know that Bob is telling the truth?
Quantum physics has a solution! In this one, the two send quanta to each other and there is a random decision. And the person who wins can also prove this. And Alice and Bob don’t even have to be in the same place.
Often this is done with photons, but we can also try it with the Qey-Gen
Luisa and Tobi explain how it works!